The Dos and Don’ts of WordPress Security

Recently, one of Oozle’s favorite security plugins, Wordfence, reported on a massive distributed brute force attack campaign. Meanwhile, here at Oozle Media, we’ve helped some of our clients secure and harden their WordPress installation after being hacked. So we’ve put together this list of Dos and Don’ts to help our clients be prepared and informed about their WordPress sites.
DON’T Panic!
 Your first instinct when you hear the word “hacked” might be to freak out. Don’t! The huge majority of the time, a hack doesn’t actually destroy your site or your brand. Your site was probably hacked to make use of your hosting’s computing power – often for things like mining Bitcoin – or to send out spam emails. In fact, a lot of the time, they’re motivated to make sure that you never find out about the hack at all. Yes, it’s bad, and we want to prevent it or fix it. The good news is that we can probably fix it relatively easily.
Your first instinct when you hear the word “hacked” might be to freak out. Don’t! The huge majority of the time, a hack doesn’t actually destroy your site or your brand. Your site was probably hacked to make use of your hosting’s computing power – often for things like mining Bitcoin – or to send out spam emails. In fact, a lot of the time, they’re motivated to make sure that you never find out about the hack at all. Yes, it’s bad, and we want to prevent it or fix it. The good news is that we can probably fix it relatively easily.
…but DON’T Ignore Your Website’s Security
Even though visitors to the site may never even notice the hack, your server could wind up flagged by anti-spam filters, or your host could sanction you for using too much processing power. Hackers love insecure websites. Even though you may not think your website would be interesting to hackers, as long as you’ve got something to offer – like a hosting server that can send emails or serve up viruses for them – your site is interesting. Lock it up!
Start off with installing a WordPress security plugin, such as Wordfence or iThemes Security.
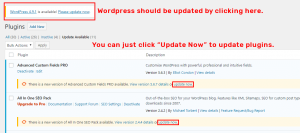
DO Keep WordPress and Plugins Updated
The simplest and most direct way to protect your site, just as yous would with your personal computer, is to keep it up-to-date. Install the latest plugin versions and keep WordPress updated. WordPress, by its nature, is a pretty secure CMS solution. There are regular security updates constantly, and the only way to take advantage is to keep everything updated.
DON’T Use the Same Password Everywhere
Wordfence realized that December’s bruteforce attack spree was probably caused by a HUGE database of passwords and logins being released on the darknet (the Internet’s black market). It turns out that most of us use the same passwords over and over across multiple sites. This is really bad for us, and really great for hackers. Change your passwords now! Remember to create a strong password.
Side Note on Passwords: If you are willing to use 2 Factor Authorization, you should. It’s an extra step in the login process, but is one of the absolute best ways to secure your login. You can check out Authy for more info on 2FA. Also, installing a CAPTCHA on your WordPress login screen (such as a Recaptcha plugin) is another way to slow down hackers.
DO Remove Unused Logins and Plugins
Unused logins and old plugins are just entry points for hackers. An old password, or an unchecked security vulnerability in a plugin, can be used to get into your site. If you don’t need it, delete it.
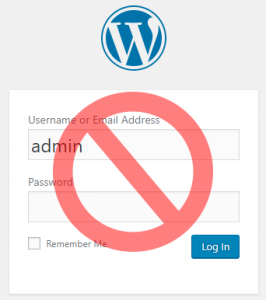
DON’T Keep Default “Admin” Username
Hackers almost always go for the default “admin” on the first try. In fact, many security plugins simply ban anyone who fails to login using “admin” because of this. If you’ve got an “admin” user on your WordPress site, you should change your username immediately.
DO Install a WordPress Backup Solution
Just in case the worst happens, and a hack destroys your site, having a good backup solution in place can be a lifesaver. Many hosting plans, such as Godaddy’s Managed WordPress hosting or WPEngine, offer automatic backups. If your hosting doesn’t offer this, it’s easy to install a backup plugin in WordPress’s admin.
Call Oozle Media If You Need Help
Oozle Media is here to help you whenever you need help. Whether you just want to be sure your site is secure, or you’ve already been hacked, we’re ready to help get your site back on track. You can contact us any time online, or call us at 877-986-6529.